CSIRT-PoliTO
INCIDENT MANAGEMENT PROCEDURE
Introduction and objectives
The plan governs the process for managing cybersecurity incidents within the university, aiming to ensure a structured, coherent, and timely approach to incident handling. Adequate incident management helps reduce the impact of adverse events, limits potential disruptions to delivered digital services, safeguards the confidentiality, integrity, and availability of processed information, and ensures transparency to users and institutional stakeholders. These objectives are set in alignment with Legislative Decree 138/2024, which requires the adoption of appropriate technical and organizational measures to maintain a high level of security for networks and information systems. In particular, the plan seeks to:
- Guarantee the identification, recording, and classification of incidents;
- Ensure a clear and traceable communication process to internal and external stakeholders involved;
- Define response and containment procedures consistent with the severity and type of incidents;
- Support the restoration of normal operational conditions within appropriate timeframes;
- Enable post‑incident analysis activities and continuous improvement of security controls;
- Fulfill current regulatory and statutory obligations regarding cybersecurity and personal data protection.
Incident management process
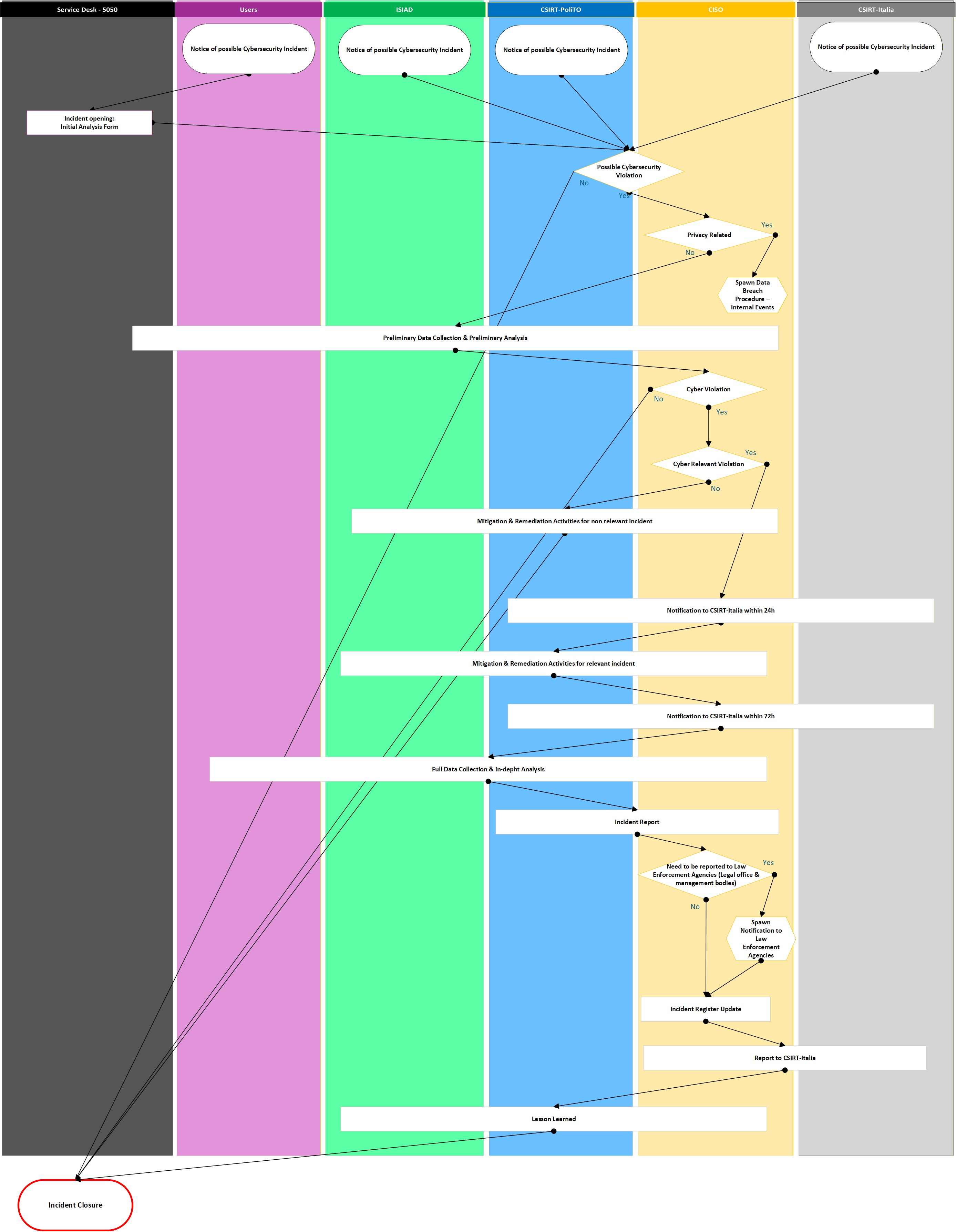
The incident‑management process is triggered when an information‑security event is classified as an incident. It must enable the timely identification of the incident, its correct classification, reduce the time required for analysis and resolution, accelerate any operational‑continuity activities, and ensure proper communication to external parties. The incident‑management process described in the following plan is organized into the following macro‑phases:
-
Prevention and Proactive Measures
This phase outlines the preventive actions and proactive measures to reduce incident risk. It includes security policies, periodic assessment of IT risk relative to critical processes, staff training, and proactive monitoring tools. -
Identification
This phase describes how security events are detected and reported, both through monitoring of security tools and via staff notifications. -
Evaluation and Classification
In this phase, incidents are analyzed and categorized based on severity and impact to determine appropriate response actions. -
Management
In this phase, the most appropriate containment and system‑restoration measures are defined and implemented. This also includes any internal and external notifications related to the event, in accordance with current regulations. -
Closure
In this phase, the incident is closed, documenting the results, recording the actions taken, and notifying the outcome to the stakeholders involved. -
Post‑Incident / Lessons Learned / Monitoring
In this phase, a final analysis of the incident is conducted to identify improvement opportunities, strengthen preventive measures, and monitor the effectiveness of the implemented actions.
Computer crimes punishable under the Penal Code (as of today)
-
Computer fraud
Article 640‑ter of the Penal Code
Consists of altering a computer system to obtain an unjust profit. Penalty: imprisonment from six months to three years and a fine from €51 to €1,032. Example: phishing. -
Illicit access to a computer or telematic system
Article 615-ter of the Penal Code
Committed by a person who enters a computer or telematic system protected by security measures, or remains therein against the expressed or tacit will of the authorized person. Penalty: imprisonment up to three years. According to the jurisprudence of the Court of Cassation, the offence is committed by those who, even if authorized, access or remain in a protected computer or telematic system, violating the conditions and limits set by the system owner to objectively delimit its access. -
Illicit possession and dissemination of access codes for computer and telematic systems
Article 615-quater of the Penal Code
Punished with imprisonment up to one year and a fine up to €5,164. The crime is committed by those who, in order to obtain a profit for themselves or others, or to cause damage to others, unlawfully obtain, reproduce, disseminate, communicate or deliver codes, passwords or other means suitable for accessing a computer or telematic system protected by security measures, or otherwise provide indications or instructions suitable for that purpose. -
Dissemination of equipment, devices or computer programs intended to damage or interrupt a computer or telematic system
Article 615‑quinquies of the Penal Code
Imprisonment up to two years and a fine up to €10,329 for the dissemination of such equipment, devices or computer programs. The crime is committed by those who obtain, produce, reproduce, import, disseminate, communicate, deliver or otherwise provide equipment, devices or computer programs with the illicit purpose of damaging a computer or telematic system, its information, data or programs contained therein or relevant to it, or of facilitating the interruption (total or partial) or alteration of its operation. -
Illicit interception, obstruction or interruption of communications
Articles 617-quater and 617-quinquies of the Penal Code
The penalty applies respectively to those who, without authorization, intercept, impede, interrupt or disclose computer communications, and to those who install equipment intended to intercept, interrupt or impede computer communications. -
Forgery, alteration, suppression of communications and damage to systems
Penal Code
The Penal Code also punishes those who falsify, alter or suppress computer communications obtained by interception (Article 617‑sexies of the Penal Code) and those who destroy, degrade or delete data, information or computer programs (Article 635‑bis of the Penal Code). Regarding the crime of violation and theft of correspondence, Law No. 547/1993, updating Article 616 of the Penal Code, specifies that “correspondence” includes postal, telegraphic, telephone, computer or telematic correspondence, or any other form of remote communication.
